
Exciting Product Updates to Enhance Your Communication Systems: 4.1.0 R2
We’re thrilled to share a series of updates and improvements we’ve rolled out to ensure that your experience with our communication solutions is not only
VitalPBX One is the all-in-one solution designed to improve your business's collaboration and communication to new levels
Ideal for any size and type of business.
Get features that cover all your call center needs
Manage multiple PBX's on the same server
Experience a fully featured Switchboard, Recording Manager, Call Center Statistics, Call Account, and Call Center Dialer, system,
The add-ons module allows you to install new modules in order to expand the PBX capabilities and add new features.
Communicate anywhere with VitXi, our full WebRTC client exclusively for your VitalPBX installation.
With VitalPBX Connect, you can make and receive business calls on your smartphone.
An advanced windows softphone for call center which integrates presence, chat, video call, BLF, and much more.
We can help with everything from implementation assistance to upgrades and production down emergencies.

Read our tutorials and guides on how to implement new tools and technologies for your business with VitalPBX here.
What Are The Risks?
Phone fraudsters are stealing billions each year through a scheme known as RSF(International Revenue Share Fraud). Estimated IRSF damages range between $4 billion and $6.1 billion

1.- Never use the same Username and password on your extensions
This is a VERY common issue, especially within the Asterisk community. Using password 101 for extension 101 is asking for big trouble. DON’T DO IT!
2.- Use the “permit=” and “deny=” lines in sip.conf
Use the “permit=” and “deny=” lines in sip.conf to only allow a small specific range of IP addresses access to extension/user in your sip.conf file. This is true even if you decide to allow inbound calls from “anywhere” (default), it won’t let those users reach any authenticated elements!
3.- Limit registration by extensions to your local subnet
Restrict the IP addresses your extensions can register onto the local subnet. Asterisk PBXs can use the ACL (permit/deny) in SIP.conf to block IP addresses. This can fend of brute force registration attempts.
4.- Make it harder for sip scanners (Set “alwaysauthreject=yes”)
Set “alwaysauthreject=yes” in your sip configuration file. What this does is prevent Asterisk from telling a sip scanner which extensions are valid by rejecting authentication requests on existing usernames with the same rejection details as with nonexistent usernames. If they can’t find you they can’t hack you!.
Another way to make it hard for SIP scanners, is to install a SIP port firewall. This will block “scanning” of port 5060 and 5061 and can disable the attempting endpoint for a specific time when it detects a violation.
5.- Change the SIP, IAX and PJSIP registry port
Generally the hackers look for if there is activity in the common ports that are 5060-5063 and 4569, is a good manner toward change these ports for less known ones. VitalPBX allows us to do this from the interface. Remember that when changing these ports you should also take into account that the devices that are registered must point to the new ports.
6.- Only allow registration by domain
VitalPBX allows us the option of only allowing registration of devices that have configured the domain of our server, this means that if a device tries to register with the ip it can not do it.
7.- Be sure to use https, when available
VitalPBX allows us to use the HTTPS interface with self-generated certificates, it is recommended to always use HTTPS in cloud environments.
8.- Change the SSH port
Generally, the port to access the Linux server console is 22 and that is what the friends of the age know, it is recommended to change this port for another less known one.
9.- Activate Firewall
It is necessary to activate the firewall on your PBX and only open the necessary ports. If you additionally have a firewall between the PBX and the Internet, it is much better.
10.- Activate Fail2ban
Any service that is exposed to the internet is susceptible to attacks from malicious parties. If your service requires authentication, illegitimate users and bots will attempt to break into your system by repeatedly trying to authenticate using different credentials. A common example of this is with SSH, which will be the subject of bot attacks that attempt to brute force common account names. Luckily, services like fail2ban were created to help us mitigate these attacks.

OpenVPN Access Server is a fully featured secure network tunneling VPN software solution that integrates OpenVPN server capabilities, enterprise management capabilities, simplified OpenVPN Connect UI, and OpenVPN Client software packages that accommodate Windows, MAC, Linux, Android, and iOS environments.
VitalPBX has a module that facilitates the integration with OpenVPN, we invite you to see the following Blog: OpenVPN With VitalPBX
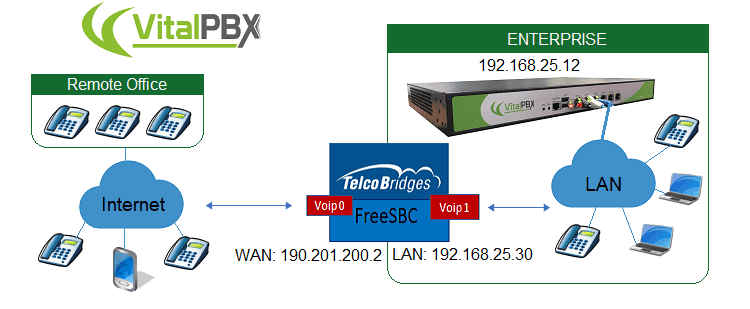
A Session Border Controller (SBC) is a network element deployed to protect SIP based, Voice over Internet Protocol (VoIP) networks.
Early deployments of SBCs were focused on the borders between two service provider networks in a peering environment. This role has now expanded to include significant deployments between a service provider’s access network and a backbone network to provide service to residential and/or enterprise customers.
VitalPBX integrates perfectly with FreeSBC, we invite you to visit the following blog: FreeSBC Integration with VitalPBX
Learn more about VitalPBX, our services and how we can help you achieve your goals in our official website.

We’re thrilled to share a series of updates and improvements we’ve rolled out to ensure that your experience with our communication solutions is not only

The VitalPBX team is thrilled to announce the rollout of VitalPBX 4.1 R1, a significant update that brings cutting-edge features and improvements to your communication

PBX System Recognized for Industry Innovation Miami, Florida, 02/27/24 — VitalPBX announced today that TMC, a global, integrated media company, has named VitalPBX Unified Communications

VitalPBX provides a robust and scalable platform, which will allow you to manage your PBX in an easy and intuitive way.