
Unlock Enhanced System Management with VitalPBX 4.1.0 R1
The VitalPBX team is thrilled to announce the rollout of VitalPBX 4.1 R1, a significant update that brings cutting-edge features and improvements to your communication
VitalPBX One is the all-in-one solution designed to improve your business's collaboration and communication to new levels
Ideal for any size and type of business.
Get features that cover all your call center needs
Manage multiple PBX's on the same server
Experience a fully featured Switchboard, Recording Manager, Call Center Statistics, Call Account, and Call Center Dialer, system,
The add-ons module allows you to install new modules in order to expand the PBX capabilities and add new features.
Communicate anywhere with VitXi, our full WebRTC client exclusively for your VitalPBX installation.
With VitalPBX Connect, you can make and receive business calls on your smartphone.
An advanced windows softphone for call center which integrates presence, chat, video call, BLF, and much more.
We can help with everything from implementation assistance to upgrades and production down emergencies.

After a long research on the internet, googling everywhere. We decided to make a manual on how to install Kamailio together with its graphical interface, dSIPRouter, to integrate it with VitalPBX.
Due to the above, we took on the task of searching for the available information and putting it together into a single guide that makes life easier for people interested in implementing Kamailio with VitalPBX. The best knowledge is the one that is transmitted to others.
What is dSIPRouter?
dSIPRouter is a Web Management GUI for Kamailio based on use case design. It allows you to quickly turn Kamailio into a platform for a SIP/PJSIP Service Provider.
What is kamailio?
The Kamailio® SIP server is a leading Open Source software for building SIP services such as a SIP proxy, SIP Presence Server, SIP location server and much more. With a rich configuration language, modularity and continuous development Kamailio is the choice for building enterprise as well as carrier solutions. Kamailio runs on Unix and Linux systems, ranging from embedded systems to large scale multi-core servers.
In this guide we are going to assume that you have already installed Debian 10, so we are going to start by installing dSIPRouter and its dependencies. To enter the Debian 10 console, you can use an ssh client such as Putty.
Make sure to set the hostname to a fully qualified domain name (FQDN) that has DNS records pointed to the server (like sbc.yourdomain.com) prior to installation. The average install time is between 4-9 minutes depending on the resources on your vm/server.
Note: You can add a “-b <version number>” to the end of the git command to install and specific version of dSIPRouter.
Install (Proxy audio (RTP) traffic)
|
At the end it will show us a message with the credentials, it is very important that you save them completely:
|
We recommend installing sngrep
|
sngrep is a tool for displaying SIP calls message flows from terminal.
It supports live capture to display realtime SIP packets and can also be used as PCAP viewer.
If for any reason when installing dSIPRouter the installation of the certificate gave an error, we recommend running it again using the following command.
|
The certificates created are shown below
|
Take a note of these two files as we will use them later.
Then go to /etc/nginx/site-available and edit the dsiprouter.conf file
|
Replace the Certificate with the one we generated in the previous step
|
Now, we proceed to restart the nginx service, and if everything is fine, it should not give any errors.
|
Once the installation of dSIPRouter is finished, we will proceed to enter through the URL that was shown at the end of step 3.1.
Now we enter the interface with the URL and credentials that it showed us at the end of the installation.
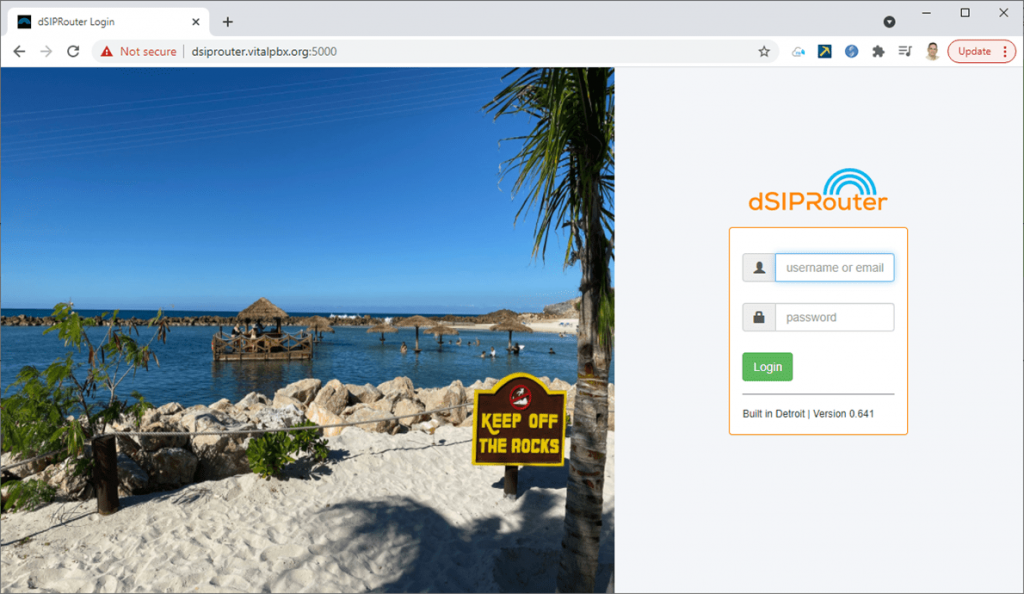
If everything is fine, the following screen will appear
Now, we will proceed to the configuration starting from the fact that we already have our VitalPBX installed on another server and that it is accessible from our dSIPRouter server.
We go to the menu on the left and press “Endpoint Groups.” Then, press the Add button that is shown at the top right, and the following form will appear:
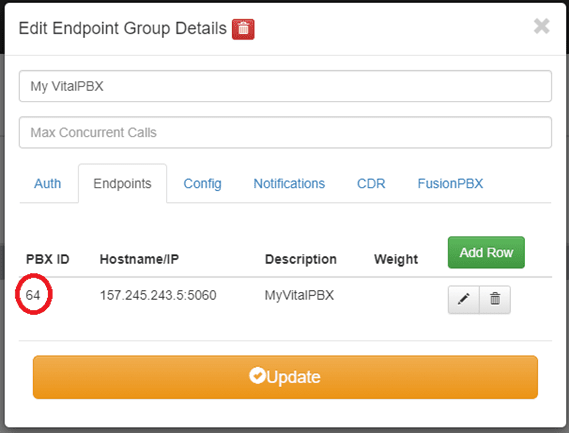
Now we proceed to press the Add button and we write down the PBX ID that is self-generated since later we will occupy it.
Now we return to the menu and press Domains and then the Add button that is at the top right and the following form will appear:
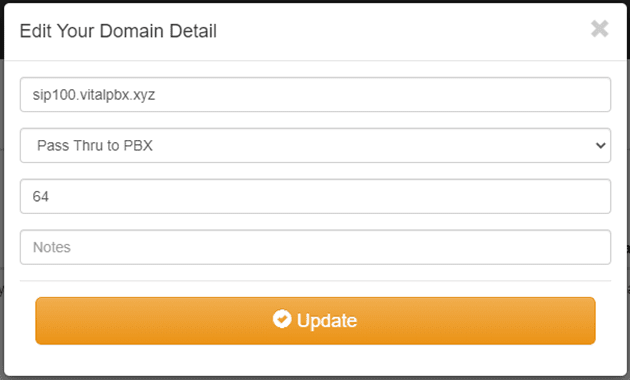
In the first field of domainA.com, we must put any domain that we are going to handle internally between dSIPRouter and VitalPBX, this domain that we write here is the one that we are going to use as the domain to register the phone. Note that in this scenario it is also necessary to declare our SIP Proxy on the phone, which would be the IP or Domain of our dSIPRouter.
Finally, we press Add.
Now we do a reload of Kamailio by pressing the top right button
Note:
If we want to use the same dSIPRouter server to protect several VitalPBX we must repeat step 4.1 and 4.2 with the values of the new VitalPBX. The new name of the SIP Proxy must be different so that when an extension is connected it knows to differentiate which VitalPBX the dSIPRouter is going to redirect.
Now we go to our VitalPBX and configure the following:
We go to SETTINGS/Technology Settings/Device Profile and create a new profile that can be called “PJSIP dSIPRouter” and configure it as shown below:
Outbound Proxy: here you must write the domain or IP of our dSIPRouter server in the following format: sip:dsiprouter-ip;\lr
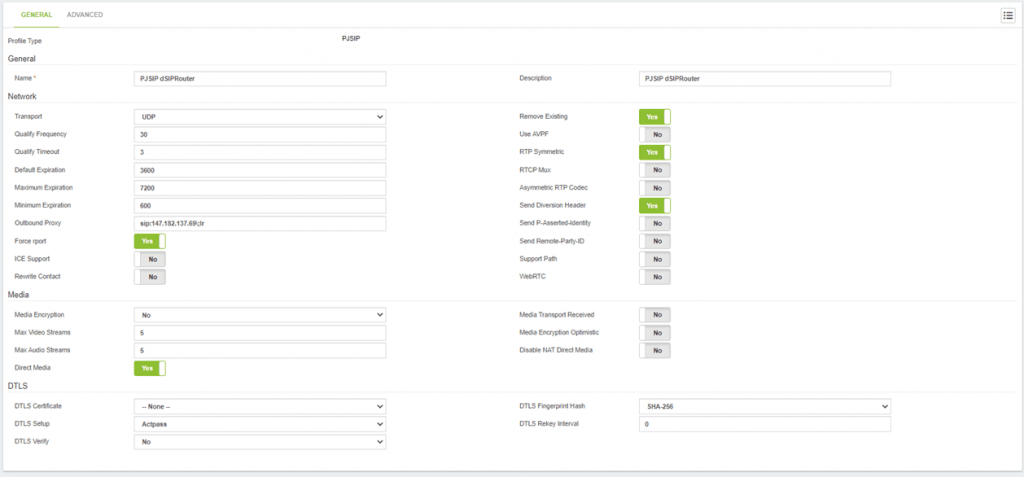
Rewrite Contact: No
We save and apply changes.
Now we go to ADMIN/Firewall/Settings and add the IP of dSIPRouter in WHITELIST.
Now we go to PBX/Extensions/Extensions and create our first PJSIP type extension with the previously created profile (“PJSIP dSIPRouter”).
Now we will proceed to configure our phone, in our case it is a Yealink T58A.
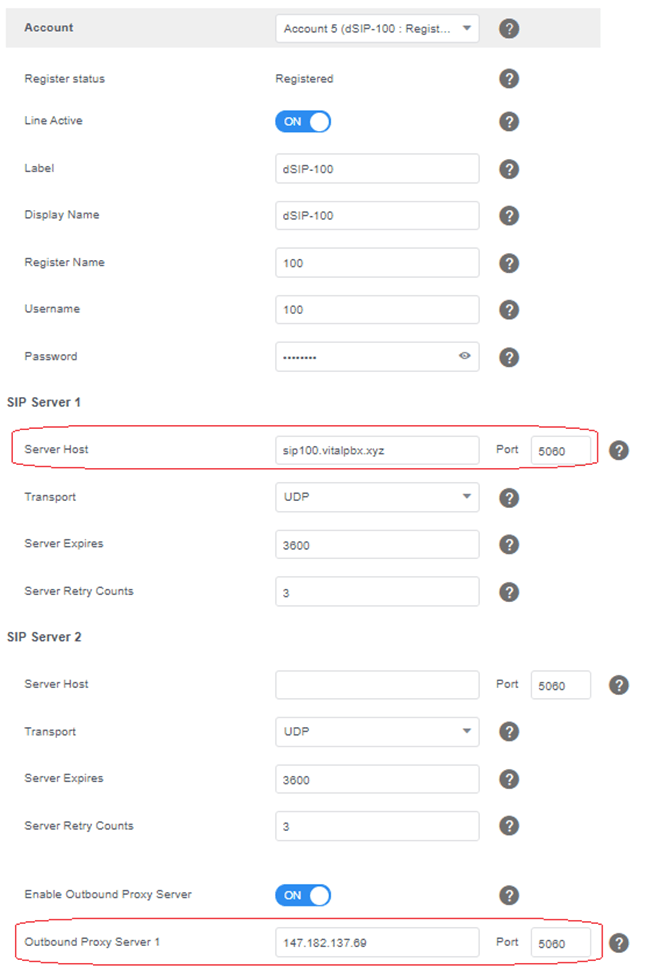
The demo parameters are the ones that we always configure in a SIP account of a phone.
Now, we are going to add an extra security in both servers for which we will follow the following steps.
Because we are only going to allow SIP/PJSIP connections from dSIPRouter, we are going to configure the firewall in such a way that only these types of connections are allowed from the dSIPRouter server.
We go to our VitalPBX server, ADMIN > Firewall > Rules, and select the SIP and PJSIP rules.
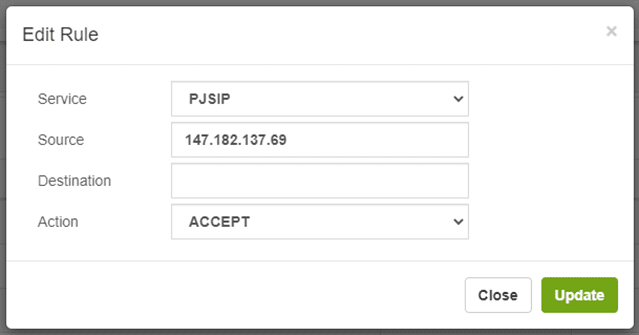
In the Source field we write the IP of our dSIPRouter server.
It is very important to avoid ssh connection attempts, because the default port is 22, all attacks are directed to this port, so we will proceed to change it.
To change the ssh port in VitalPBX it is necessary to first add in the VitalPBX firewall access from any IP to the new port, for which we go to ADMIN/Firewall/Service and add a new rule that can be called ssh-my- port.
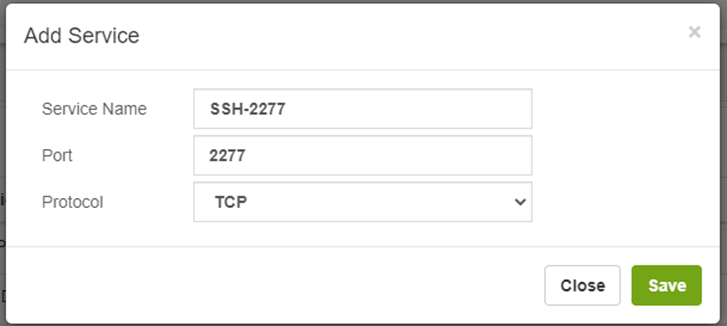
Later we go to ADMIN/Firewall/Rules and add the rule associated with this service.
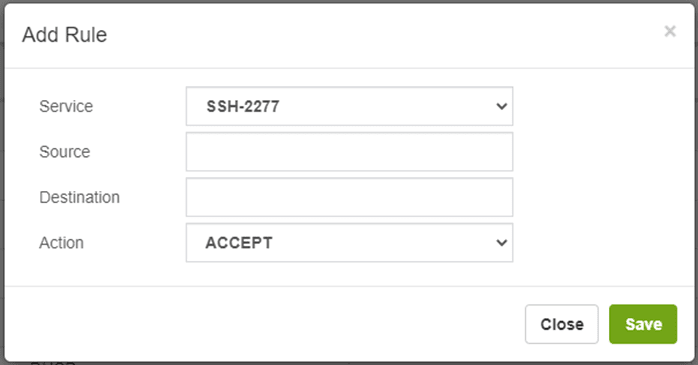
Now we apply changes.
We proceed to the console and edit the /etc/ssh/sshd_config file
|
Locate the line “#Port 22”, remove the “#” and replace the 22 with the new port, it should look like this:
|
Now restart the ssh service
|
We already have secured our server a bit more at the SSH level.
We proceed to the console and edit the /etc/ssh/sshd_config file
|
Locate the line “#Port 22”, remove the “#” and replace the 22 with the new port, it should look like this:
|
Later we add a new rule to allow ssh connections through the new port.
|
Now restart the ssh service
|
We now have secured our server a bit more at the SSH level.
We hope you succeed in this implementation. Feel free to contact us through our forum if you have any questions, https://forums.new.vitalpbx.org.
Note:
Source of information: dSIPRouter website, Kamailio website
Thanks to Luciano Moreira who shared very valuable information to make this Blog.

The VitalPBX team is thrilled to announce the rollout of VitalPBX 4.1 R1, a significant update that brings cutting-edge features and improvements to your communication

PBX System Recognized for Industry Innovation Miami, Florida, 02/27/24 — VitalPBX announced today that TMC, a global, integrated media company, has named VitalPBX Unified Communications

Introduction The Private Branch Exchange, or PBX, has been a fundamental pillar in business communication for decades. As technology has advanced, so have the capabilities

VitalPBX provides a robust and scalable platform, which will allow you to manage your PBX in an easy and intuitive way.